HBSRESOURCES
Infographics
Insight at a glance: technology solutions simplified.
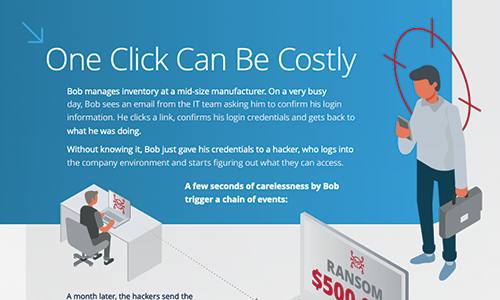
The Cost of an Email Phishing Attack
It only takes a few seconds to trigger a chain of events that could be detrimental to your organization. This infographic breaks down how one click could quickly turn into thousands of dollars.
View Infographic
View Infographic
Spotting Business Email Compromise
BEC attacks use sophisticated techniques that can trick all but the most attentive email users. Attackers typically impersonate a legitimate contact asking for a transfer of funds. But when victims send the money, it lands in a bank account controlled by the bad guys. This infographic shows the key stages of business email compromise.
View Infographic
View Infographic
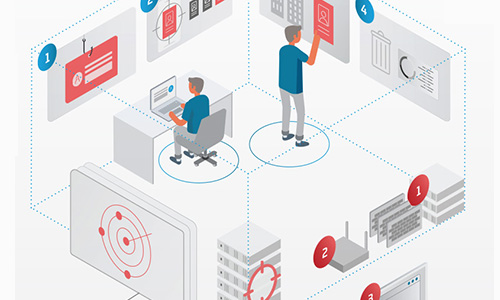
Types of Penetration Testing
A thorough penetration testing campaign involves social engineering, vulnerability scanning, and the manual hacking of computer systems, networks, and web applications. This overview shows how a professional pen testing team tries to exploit a variety of attack vectors, just as a real hacker would.
View Infographic
View Infographic
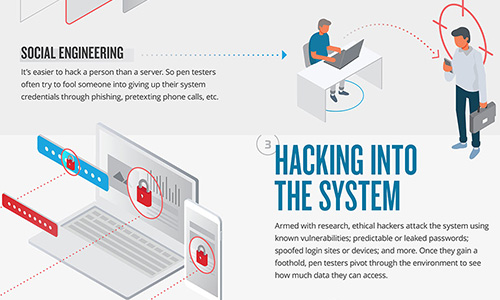
Penetration Testing Explained
Penetration testing provides a real-world test of your security posture by sending an ethical hacker to break in using the same techniques as real bad guys.
View Infographic
View Infographic






