SMiShing Attacks: How to Identify and Respond
- Written by: Matthew McGill

Among the many threats to employee internet security is “SMiShing,” in which bad actors try to steal personal or company data or set up a scam via text.
Imagine if one of your employees got this message an hour ago:
Jeff, this is HR. ACME’s corporate VISA card requires that you verify your PIN for verification that you are an authorized user. Please protect yourself and ACME’s account at once by simply replying to this message with your PIN.
How confident are you that Jeff did not dutifully and swiftly reply to the urgent message from “your” company with her corporate PIN? How confident are you that the attacker – posing as ACME HR -- didn’t ask for more personal or corporate information from Jeff before she caught on to the scam?
Welcome to one of the fastest-growing innovations in phishing: Short Message Service (SMS), text-based phishing…or SMiSHing, for short.
By now, you have likely been SMiShed multiple times, possibly even multiple times this week! Social engineering criminals have found that the ease and convenience of texting for legitimate purposes has created a target-rich environment for victimizing unsuspecting people.
A Real-Life Experience with an SMS Message Phishing Attack
A few years ago, 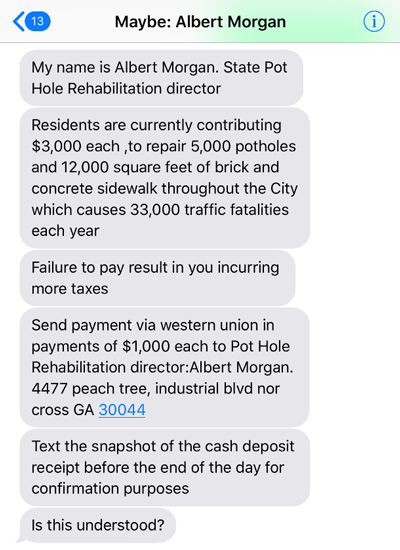 I received a text message from an unknown number containing my full name and asking the simple question of “how are you?”
I received a text message from an unknown number containing my full name and asking the simple question of “how are you?”
As a cybersecurity professional, I decided to – with caution – investigate the obvious attempt SMiSHing. It was quite an interesting text message to receive, especially since it contained my full legal name. Already a little suspicious, I responded with “Hello, who is this?” to validate that it wasn’t someone I recently met. The conversation that ensued between me and “Mr. A Morgan” was very clearly an engagement with a social engineer – not a bot – but a real human. I knew and understood immediately that this text message was not legitimate, but I proceeded with the conversation to accomplish a few objectives: consume this person’s time from targeting other individuals and learn how social engineers were trying to steal money/information in 2018 via this avenue of communication.
Keep an Eye Out for These SMiShing Tactics
Social engineers will use many tactics to try and coerce information out of us, attempting to catch our eye through tempting offers or the use of fear. The following points are a series of tactics that social engineers may employ to obtain such information.
- Social engineers know how people work and operate, so they very clearly and intentionally craft attacks to play on some of our biggest psychological fears and wants. They also understand that not everyone will “buy into” their scheme, so they tend to stay broad in their language. Avoid ambiguous texts that fail to mention specific locations, organizations, websites, names, etc.
- Mention of Western Union. For whatever reason, payments through Western Union tend to be the most popular form of money transfer in such attacks. If a text message says “wire money” via Western Union, this should cause you to raise an eyebrow.
- Never click on links or navigate to unknown websites as prompted by an attacker. Websites pose a much greater risk to you and your personal information.
- Legitimate physical locations or addresses will sometimes be included to lend realism. You can look up 4477 Peachtree Industrial Blvd. Norcross, GA 30044, and a real location (with the actual ZIP of 30071) will appear – as vacant land for sale. Not exactly the sort of “pot hole rehabilitation” company you might expect in the Midwest.
Four years later, these principles remain in effect, but the attacks have become more sophisticated and targeted. Employees who once believed themselves socially immune to the grammar-challenged texts of the late 2010s are now succumbing to the deceptive requests in droves. In 2021 they were a problem to the tune of $44 billion in losses, just in the USThe US alone lost $44 billion from them in 2021. According to the FBI, the situation is only getting worse. CNET reports that smishing attempts increased 24% in the United States alone and 69% globally. The average consumer now receives 19.5 spam texts per month, double the rate three years ago.
Extending the “ACME” Employee Scenario
Let’s play out the scenario with Jeff just a little further:
Jeff: Sorry, wrong number.
Attacker: This is the number we have listed as the account. If it is a wrong number, ACME’s corporate VISA card will be suspended for all users indefinitely. Please enter your PIN at the following secure link: securelink.visa@ACME
Jeff: Can you verify that this is ACME?
Attacker: ACME, Inc. FEIN: 123456789. This is Amy in HR. We talked at the company event this summer.
Jeff: Oh, hi Amy! So sorry. I’ll get you the PIN right away.
Much like some of the more gifted mentalists and psychics on television, SMiShers have perfected the art of “cold reading” in their attempts to socially engineer others, which means that if they guess vague events correctly, they confirm to the target that they might be trustworthy. If they guess incorrectly (perhaps there is no Amy who works in HR – perhaps there were no company events last summer), Jeff will likely (at least briefly) doubt her memory of things or be embarrassed that she doesn’t remember ever meeting friendly, helpful “Dave from ACME.” The truth is that, even though Jeff may not initially have given away any useful information to “Amy”, even her initial “wrong number” response confirmed to “Amy” that the number had a live target on the other end. And that left Jeff open to further and more harmful social engineering techniques.
Protecting Your Employees from SMiShing
So, what can ACME – or you – do for employees?
- If possible, enact some sort of clear “no text” policy with your employees. Assure them that your company will never contact them by text in such a way that asks for a direct response back via text. Corporate announcements or other “FYI” texts are probably okay, but if you need further action in communications, make sure employees know, well ahead of time and by corporate policy that they are to do so by emailing a known, pre-existing corporate in-box or by calling a known, pre-existing number. Make sure employees know that they are NEVER to text any corporate information to anyone under any circumstances.
- Set up a safe forwarding system for employees to easily forward suspected SMiShing and phishing attempts to a monitored in-box. Then make sure known or persistent SMiShing attempts are publicized to your employees regularly, if for nothing else but to keep their natural” SMiShing-sense” up and monitoring for threats.
- Make sure employees are aware of an “immediate error amnesty” policy or process, so that employees feel safe and encouraged to admit SMiShing errors at once without fear of punishment. The only thing worse than a successful SMiSh is an unreported successful SMiSh!
- Set up professionally designed artificial SMiShing tests for employees on a somewhat regular basis. Measure the response rate. Let employees know – privately - when they fail the test. Report the statistics to your employees. Hopefully, over time, you can measure the improved resilience of your staff against SMiShing.
- Encourage employees, that if they are ever suspicious about a text message they receive, to block the number at once. There are websites and online tools, such as the FTC Complaint Assistant website, that allows you to report unwanted and unwarranted phone numbers.
- Encourage employees to – independent of the texting stream – to always try to validate the identity of the individual attempting the SMiSh. No financial institution or software company will ever contact employees and request information in this way. Never give out personal or digital information unless the correct identity has been proven and confirmed.
Social engineering is nothing new, and yet it continues to be one of the most attempted and successful ways attackers obtain information. It is important to stay alert to these attacks and their evolution in an ever-increasing digital age. Knowing the risks associated with personal forms of communication can help you stay ahead of the curve and avoid leakage of proprietary business intelligence. It is very important to take a proactive, risk-based approach to social engineering and the various phishing attack vectors. HBS offers a suite of services ranging from security awareness training to the actual execution of ethical social engineering campaigns to address these concerns and help your organization mitigate its overall risk.






