Infographic: Types of Penetration Testing
- Written by: Trevor Meers
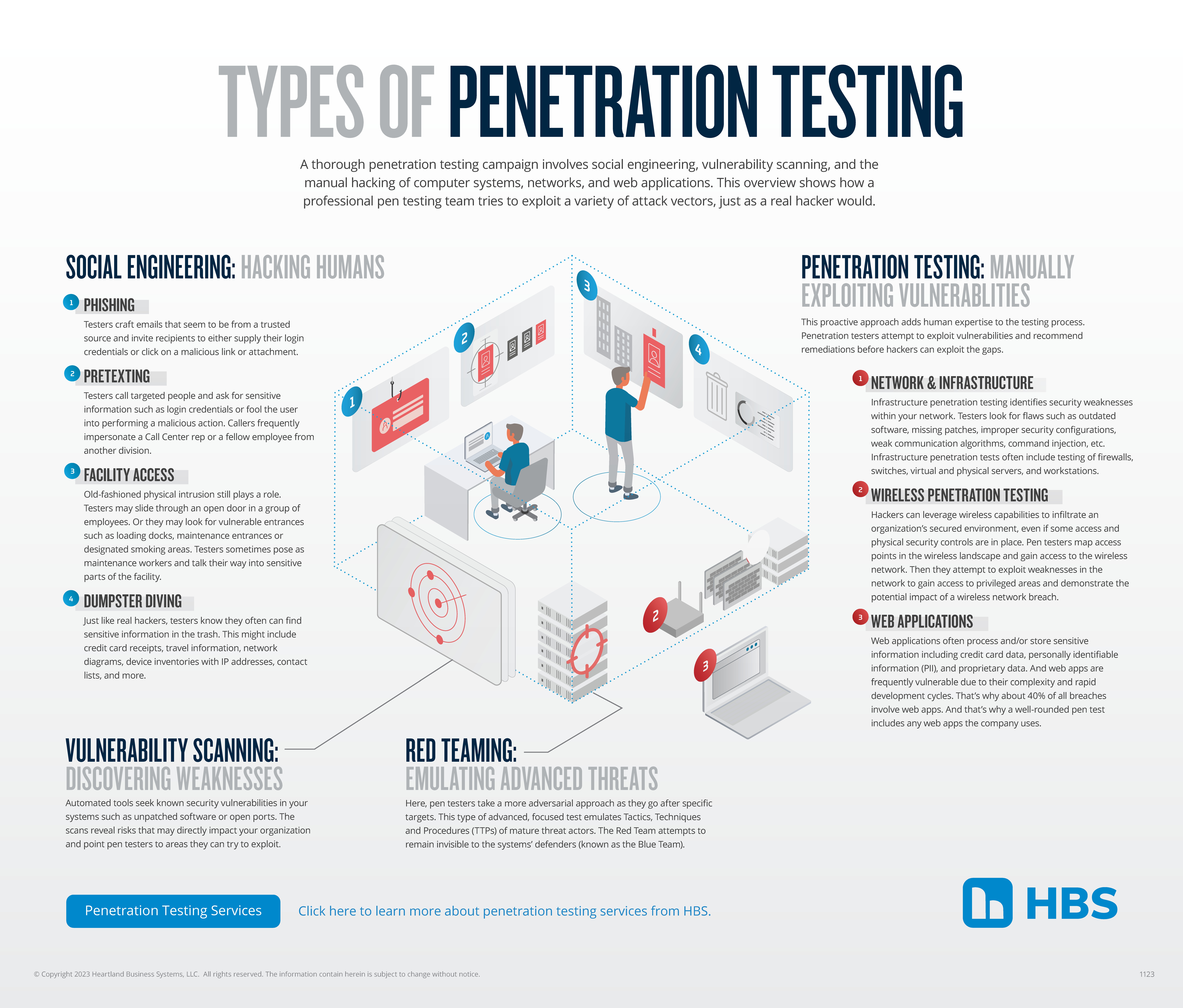
A thorough penetration testing campaign involves social engineering, vulnerability scanning, and the manual hacking of computer systems, networks, and web applications. This overview shows how a professional team uses multiple types of penetration testing to exploit a variety of attack vectors, just as a real hacker would.
Social Engineering: Hacking Humans
- Phishing
Penetration testers craft emails that seem to be from a trusted source and invite recipients to either supply their login credentials or click on a malicious link or attachment. - Pretexting
Penetration testers call targeted people and ask for sensitive information such as login credentials or fool the user into performing a malicious action. Callers frequently impersonate a Call Center rep or a fellow employee from another division. - Facility Access
Old-fashioned physical intrusion still plays a role. Penetration testers may slide through an open door in a group of employees. Or they may look for vulnerable entrances such as loading docks, maintenance entrances or designated smoking areas. Testers sometimes pose as maintenance workers and talk their way into sensitive parts of the facility. - Dumpster Diving
Just like real hackers, testers know they often can find sensitive information in the trash. This might include credit card receipts, travel information, network diagrams, device inventories with IP addresses, contact lists, and more.
Vulnerability Scanning: Discovering Weaknesses
Automated tools seek known security vulnerabilities in your systems such as unpatched software or open ports. The scans reveal risks that may directly impact your organization and point penetration testers to areas they can try to exploit.
Penetration Testing: Manually Exploiting Vulnerabilities
- Network & Infrastructure
Infrastructure penetration testing identifies security weaknesses within your network. Testers look for flaws such as outdated software, missing patches, improper security configurations, weak communication algorithms, command injection, etc. Infrastructure penetration tests often include testing of firewalls, switches, virtual and physical servers, and workstations. - Wireless Penetration Testing
Hackers can leverage wireless capabilities to infiltrate an organization’s secured environment, even if some access and physical security controls are in place. Pen testers map access points in the wireless landscape and gain access to the wireless network. Then they attempt to exploit weaknesses in the network to gain access to privileged areas and demonstrate the potential impact of a wireless network breach - Web Applications
Web applications often process and/or store sensitive information including credit card data, personally identifiable information (PII), and proprietary data. And web apps are frequently vulnerable due to their complexity and rapid development cycles. That’s why about 40% of all breaches involve web apps. And that’s why a well-rounded pen test includes any web apps the company uses.
Red Teaming: Emulating Advanced Threats
Here, penetration testers take a more adversarial approach as they go after specific targets. This type of advanced, focused test emulates Tactics, Techniques and Procedures (TTPs) of mature threat actors. The Red Team attempts to remain invisible to the systems’ defenders (known as the Blue Team).
To learn more about HBS's penetration testing services, contact us today.
Never miss a story
Get the latest technology insights from HBS, right in your inbox.
By entering your email, you agree to receive HBS emails and agree to our Terms & Conditions and Privacy Policy.






