Don’t Get Hooked by Phishing: Understanding Internet Domains
- Written by: Jeff Hudgens

Phishing has pumped up its frequency to being present in 36% of breaches (up from 25% last year).
2021 Verizon Data Breach Investigations Report
Network end users are frontline defenders that form a critical component of an organization's information security program. That’s why all cybersecurity training materials include sections on how to spot phishing, which is both rampant and increasingly sophisticated in the methods used to lure victims. When our consultants evaluate risk within an organization and discuss their phishing awareness and training efforts, we typically see advice such as “Don't click on suspicious links” and “Hover the mouse pointer over links in an email to check whether it is legitimate.” But how do you know whether a link and the associated Uniform Resource Locator (URL) lead to a legitimate site?
To evaluate links and URLs, you should understand generic Top-Level Domains (gTLDs), country code TLDs (ccTLDs), and other types of Internet domains. This article covers the basics about reading and interpreting links/URLs.
What Does "www1" Mean?
A web address looks pretty suspicious if you see “www1” or “www2” (or some other number) in the URL. But that's not a definite red flag. Some web sites may be very popular and, therefore, have multiple servers working in a load-balancing configuration to serve content when requested. Some companies choose to number their servers. So, if you see a www1 or www2, you’re just seeing which server # among multiple servers is providing the content. Seeing a www1, www2, etc., is not in itself an indicator of a phishing site.
One way to teach users to look for indicators like these is by developing a customized training program that includes phishing awareness and testing. A training consultant can develop a set of simulated phishing messages that help users learn to spot red flags. When users click the simulated malicious links, the program can point them to additional training.
How Links/URLs are Formed
So what’s the key to reading URLs in links? The basic answer is that interpreting the URL means focusing on the important stuff between the double forward-slash “//” and the first single slash, primarily in the highlighted area shown below.
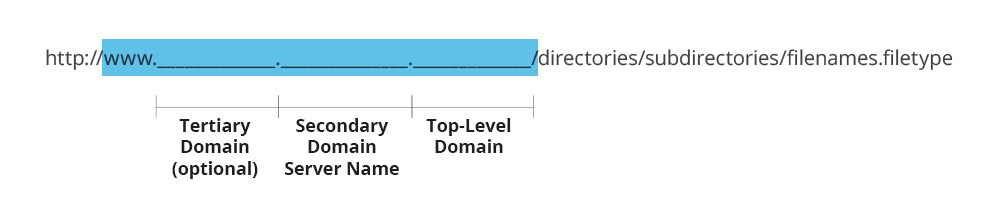
Note: The framework above is the basic URL breakdown. In place of http:// or https://, you may see ftp:// or news://. These are different types of transfer protocols. In addition, though “www” appears in many URLs, it is not a required component. You may see additional fields prior to the generic top-level domain and secondary domain/server name. (After the first single forward slash, you’ll find less critical things such as directories, subdirectories, filenames and file types.)
Example Links/URLs
1. http://www.amazon.com
This is a well-known site, and the URL doesn’t include any suspicious modifications.
Assessment: LEGIT!
2. http://www.ama.zon.com/gp/cart/view.html/ref=nav_cart
URLs can be formed in almost any fashion, which makes it easy for site owners to build unique site names. It also makes it easy for phishers to build site names that closely approximate legitimate site names.
In this example, a period makes all the difference. If a person clicked on the link above, they wouldn’t go to amazon.com. The link leads to the site zon.com, which could be a site registered by phishers.
Assessment: SUSPECT!
3. http://[email protected]/catalog
In this case, a person would be directed to IP address 66.161.153.155, not amazon.com. If you see a link/URL with an “@” sign, be particularly careful. Phishers routinely use this URL-manipulation tactic.
Assessment: SUSPECT!
4. http://209.131.36.158/amazon.com/index.jsp
This URL is somewhat similar in function to #3 above. It leads to the IP address, not amazon.com, which is listed after the first single forward slash.
Assessment: SUSPECT!
5. http://www.google.com/url?q=http://www.badsite.com
This URL would refer a person from one site (in this case, google.com) to another site, badsite.com (note the “=http://” nomenclature that allows this). Referrals are not in themselves bad, but a referral could lead to a phishing site. In this case, badsite.com doesn’t look legitimate.
Assessment: SUSPECT!
To help users quickly determine the top-level and secondary domains within a URL, some companies and organizations have started to use “domain highlighting.” When a user visits a site, part of the URL will dim after a few seconds, leaving the top-level and secondary domains dark. For example:
![]()
It’s always good to look for these signs of a legitimate, secure site:
- closed padlock
- https://
- company name highlighted in green within the URL (such as in the PayPal example above).
If a site’s certificate is expired or otherwise invalid, some browsers, such as Internet Explorer and Firefox, or security services, will warn users. Is it safe to proceed through the warning? In this case, use other available indicators (review the URL again) to help determine whether the site is legitimate. If in doubt, do not proceed.
Why Country Domains Matter
Fifty-four countries have chosen to allow their ccTLDs to be used for commercial purposes. For example, .co, the ccTLD for Colombia, can be used in place of .com. It’s very popular, due to the burgeoning .com domain, and allows businesses to have alternative ways to form website names.
Have you seen the URL http://o.co? That’s Overstock.com providing an alternate way for you to get to the company through your browser.
You may have seen youtu.be. That’s a legitimate URL, registered by Google using Belgium’s ccTLD, .be.
Much of the entertainment industry uses Tavalu’s ccTLD, .TV. It’s a great way for the island nation to make money.
When trying to determine whether a site is legitimate, realize that many ccTLDs are also used for commercial purposes. What looks like a suspicious site could be, in fact, legitimate. However, ccTLDs can also be used to form names for phishing sites, so when in doubt, don’t click!
A Short History of Generic Top-Level Domains
We are all used to seeing gTLDs. We use them almost every day, including familiar ones such as .com, .gov and .edu. They are a key part of the structure of the Internet. They are also well understood by phishers, who manipulate URLs for fraudulent use. To best assess links within emails, as well as URLs within browsers, it’s good to know how the various domains have evolved and how they work.
In 1984, Request for Comments (RFC) 920 was used to define the original “general purpose domains”: .com, .gov, .mil, .edu, and .org. Another domain, .net, was added in early 1985 and is also considered one of the “original” domains. In 1988, .int (international) was added to meet the North Atlantic Treaty Organization’s request for a domain. Over the years, other domains were added, such as .biz and .info (2001). By early 2011, 22 gTLDs had been established. In June 2011, the Internet Corporation for Assigned Names and Numbers (ICANN) voted to remove many of the restrictions on gTLD applications and implementation, effectively opening the door for almost any gTLD to be used. Under the new rules, there are currently about 1,500 gTLDs, including .auto, .computer, .network, .social, .pizza, .organic, registered and cleared for use on the Internet. According to some security experts, this evolution in gTLDs is considered a gift to phishers because it will allow them to form a multitude of new phishing websites. For a full listing of the expanded gTLDs, see the Internet Assigned Numbers Authority (IANA) Root Zone Database (https://www.iana.org/domains/root/db).
Country Code TLDs
Country code TLDs are also part of many URLs, and, therefore, one can expect to see them in links on occasion. Countries have ccTLDs to help distinguish what country a site is registered in or originates from. For example, the ccTLD for the United States, .us, is often used by state and local governments. Other ccTLD examples are Australia, .au; Japan, .jp; and United Kingdom, .uk. When reading a link or URL, realize that the location of the ccTLD within the URL could shift (at the end of a URL, such as http://www.gov.uk, or earlier in a URL, such as https ://uk.news.yahoo.com).
Conclusion
Phishing continues to be a global problem, exacerbated by users who are unaware of phishing tactics, increasingly sophisticated phishing methods, and now, an increasing set of generic Top-Level Domains. Though links in emails aren’t phishers’ only method, they’re very common. To reduce the risks posed by phishing, you should know how to interpret links and the associated URLs.
If you are interested in learning more about social engineering, awareness and training, and risk assessment services, please contact us today.






