Why Intrusion Detection and Prevention Systems are Still Important
- Written by: Trevor Meers
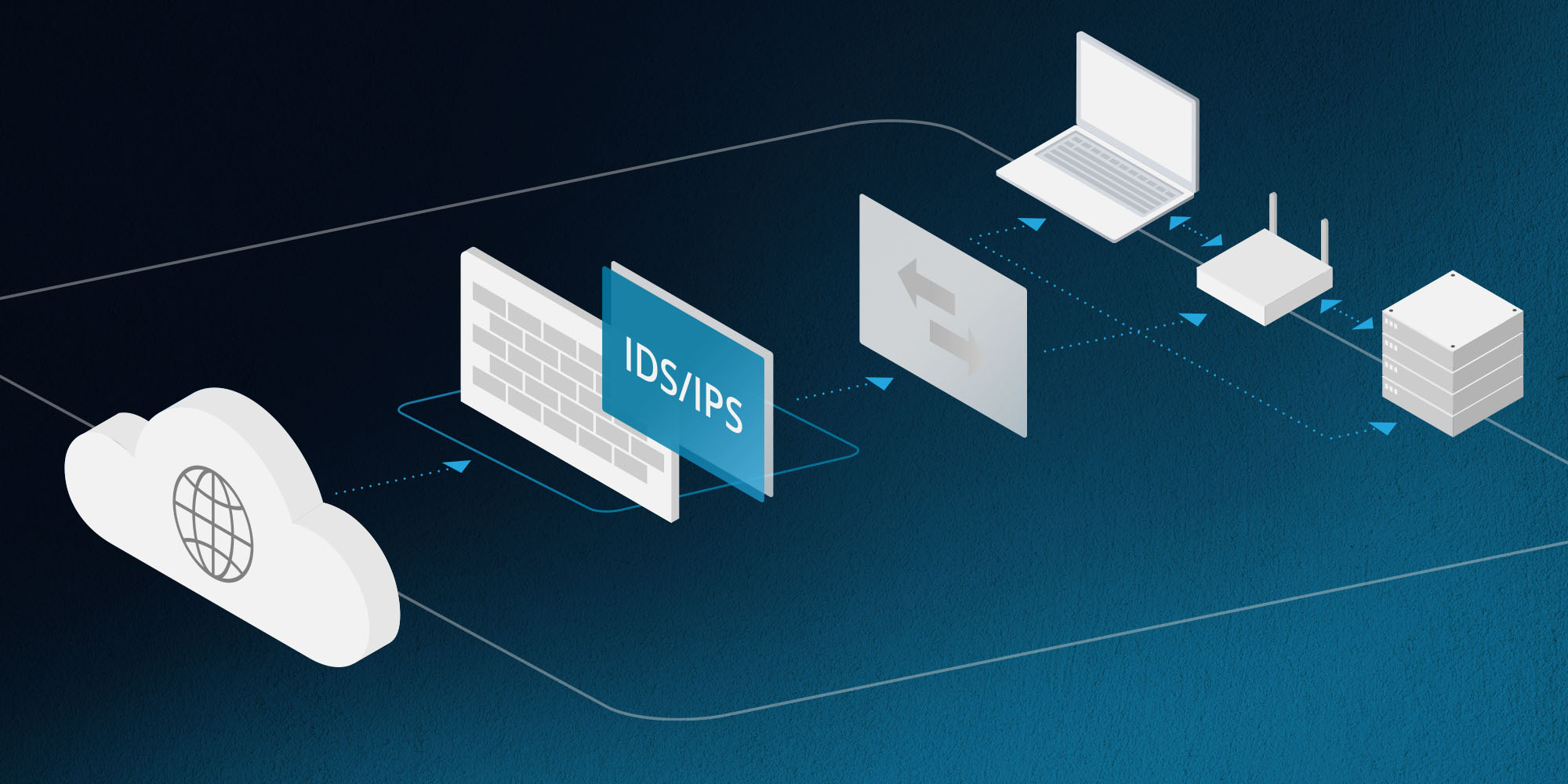
At one time, everyone considered intrusion detection (IDS) or prevention (IPS) systems critical to overall information security success. But in recent years, observers keep declaring IDS/IPS dead, only to see it keep hanging on. And while we’re still not ready to bury IDS/IPS today, we DO urge you to consider how you’re deploying these tools within your overall information security strategy. Without proper tuning and deployment, IDS/IPS solutions can't do their jobs properly. And the current landscape of cloud computing and dispersed workforces means protection tied to a firewall misses a lot of activity. Read on to learn how to properly leverage IDS/IPS in a modern environment.
How IDS/IPS Works
The goal of IDS is to detect cyberattacks by analyzing the signature of data packets as they traverse the network. When the system detects a suspicious packet, it generates an alert. IDS is a passive tool that simply detects and alerts. IPS goes a step farther by adding an active protection method of adapting to the threat and blocking the traffic from reaching the intended victim host. Most IDS/IPS solutions are now available as a bundle with your firewall subscription.
Weaknesses in IDS and IPS Systems
To effectively use IDS/IPS systems, you should be aware of a couple of inherent limitations:
- They rely on signatures, which means they only watch for what you tell them to. These systems require constant tuning to keep up with changing attack vectors used by cybercriminals. Tuning signatures to eliminate false positives and alert fatigue is a full-time job. In fact, there’s an entire industry providing these services. Even if you purchase these feeds of updated signatures, you still need to test and tweak them to match each unique environment. This explains why most IT teams use IDS rather than IPS. They don’t have time to tune the system, so they just skip the protection tools rather than risk constant business interruptions caused by false positives.
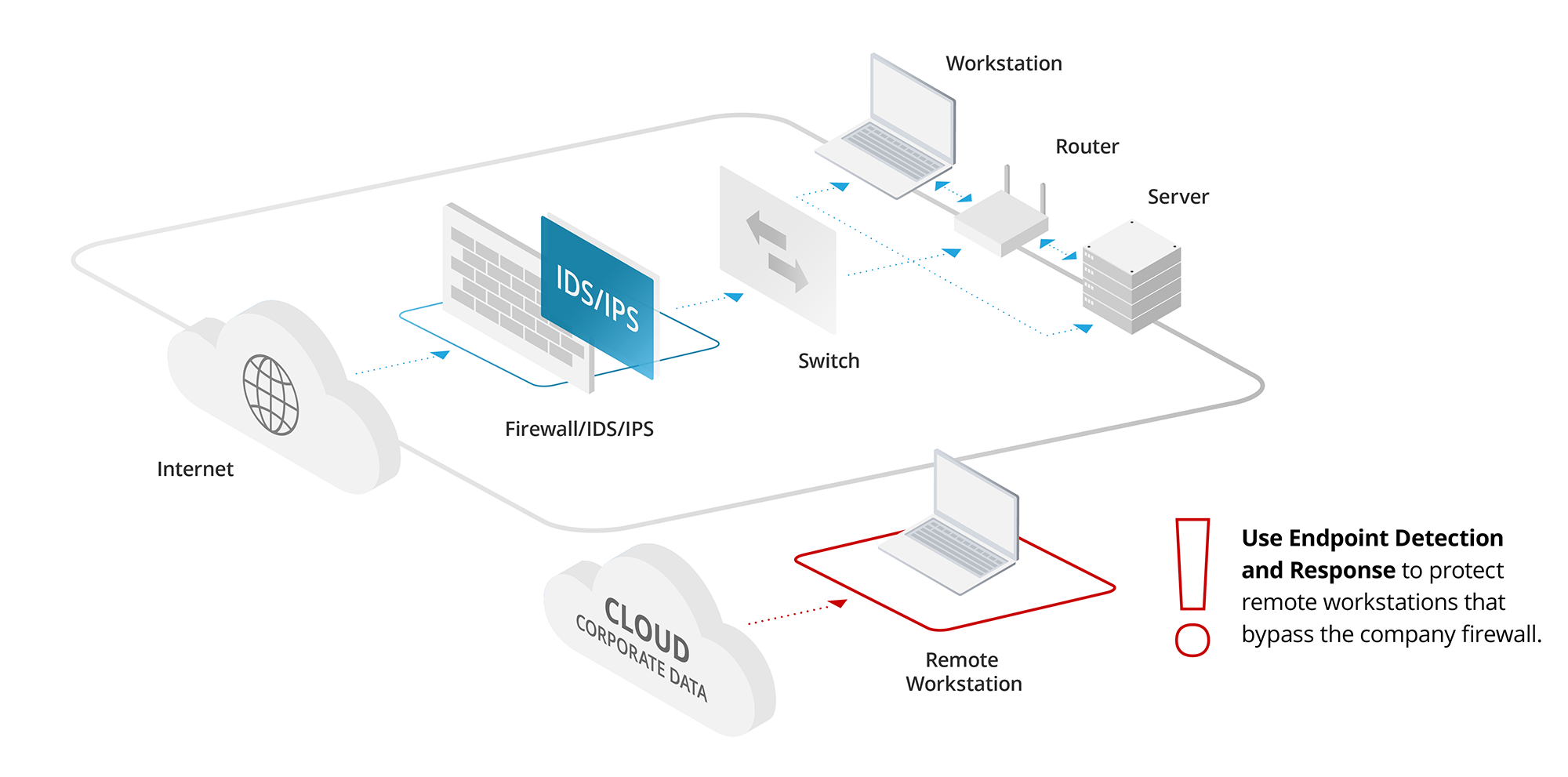
- They can see only traffic that passes by them. All too often, we see IDS/IPS implementations provide a false sense of security to an organization because of poor network design. Organizations frequently rely on a unified threat management (UTM) type of firewall to provide their IPS. In that setup, the IPS sees only the traffic that is routed through the firewall. Most of the time, this is only internet traffic to the DMZ servers (such as websites and email) and outbound traffic to the internet from the workstations on the local network.
While a UTM setup is a start, it leaves major gaps in coverage. The setup typically lacks monitoring within security zones or between local workstations, servers and remote workforces. You may have compromised systems attempting to breach other internal systems, but you can’t see it because the IPS isn’t privy to the traffic on those network segments without it passing through the IDS/IPS.
How to Use IDS/IPS Effectively
Follow these steps to ensure that these tools provide the protection you’re expecting:
- Get a risk assessment. Many organizations implement IDS/IPS simply to fulfill a compliance checkbox. But you need a full information security risk assessment to get a true picture of your organizational risk. Plus, you may still be non-compliant with IDS/IPS in place because most compliance requirements such as HIPAA, PCI, FISMA, etc. require a risk assessment.
- Ingest IDS/IPS data into your SIEM. Your SIEM provides a centralized log and alerting system for the entire environment. An IDS keeps its own logs, but how often are you looking at them? By ingesting the IDS/IPS data into your SIEM, you’ll have a clear look at what’s happening. This process will probably show you just how noisy most IDS/IPS’ are in terms of alerts generated, which will probably motivate you to do some tuning.
- Add EDR (endpoint detection and response). Protection tied to your firewall doesn’t account for today’s distributed workforces. Many of your users now work remotely, which means their activities never pass through your corporate firewall. The solution is EDR, which bundles active detection and response into each workstation. A full Managed Extended Detection and Response (XDR) system protects workstations, IoT devices, BYOD issues and more.
- Leverage XDR to make IDS/IPS more effective. With the detailed information and correlation provided by XDR, you’ll be able to spot poorly tuned IDS/IPS, antivirus and other tools and make the right adjustments.
For help reviewing your security system’s architecture, contact us today.






