Benefits of Log Consolidation in a SIEM Environment
- Written by: Greg Applebee
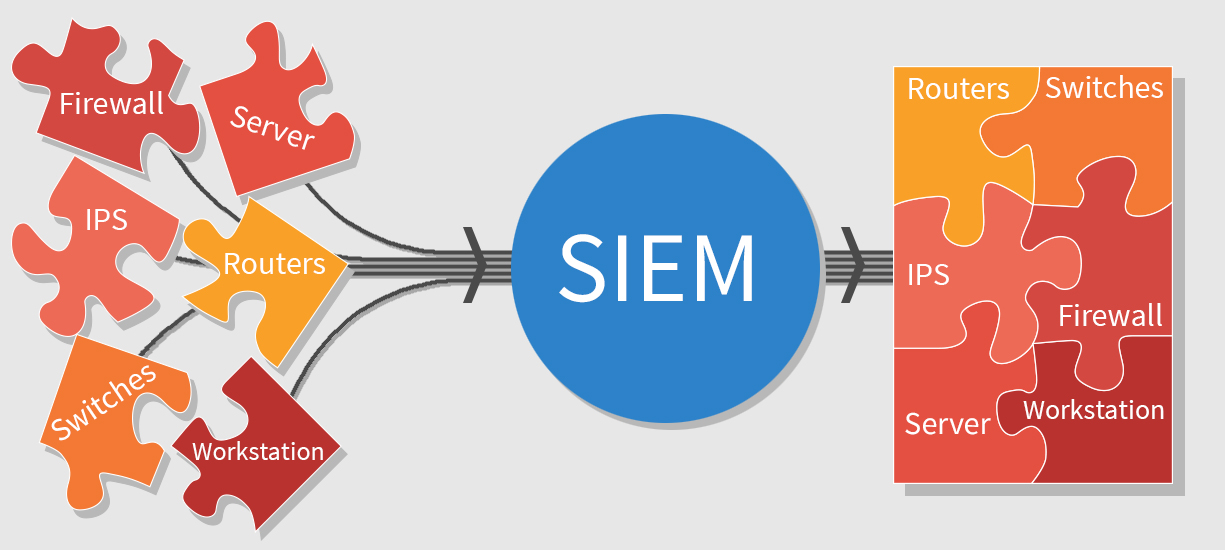
For those not familiar with SIEM (Security Information and Event Management), it is a security strategy that seeks to efficiently consolidate and manage network data. The centralized view of all data makes it easier to identify security threats and track them throughout an environment. This is often done through a SIEM solution, an application that gathers data and organizes it into a manageable repository.
Reacting to Malicious Traffic
A concern for all networks is malicious traffic. We can’t always prevent criminals from attempting to attack our systems, but we can add safeguards to detect malicious or unwanted traffic and prevent them from entering our network. A SIEM solution exponentially increases the chances of successfully identifying this type of behavior due to its advanced correlation between so many different types of logs from various devices. Without SIEM, identifying a handful of malicious logs that were generated in combination with thousands of others per second drastically reduces the ability to identify anything accurately.
Handling Malicious Traffic without SIEM
Managing alerts and incidents without SIEM can be unwieldly. You may get an alert from your antivirus, or see in a report from your firewall, that traffic determined to be malicious has been detected entering your network. This information is helpful, but it doesn’t tell us how the traffic entered our systems, what else it has gotten access to, or if it is still an issue. At this point your options are to either keep an eye out for other indicators of virus or malware activity, or you must manually access the logs from each infected device and sift through the data to find common issues.
Addressing malicious traffic can be done manually, but it is not very efficient and can be rather ineffective. Fortunately, there are technologies available that simplify this type of work. You may be saying to yourself “I bet the SIEM option is more costly,” but when you take a look at all of the benefits and cost saving from SIEM, you will see that the manual method can be much more expensive, not to mention if a breach occurs and goes undetected.
Relying on only a handful of independent alerts from a firewall or AV server is comparable to only having one or two smoke detectors in your home or business. A fire could be burning through half the building before any warning or detection occurs.
Malicious Traffic with SIEM
Let’s look into that same malicious traffic, but this time using a SIEM client. Remember, the SIEM solution aggregates and manages all incidents, from every device, in one spot. This correlation gives us a better understanding of what is happening in the network. In a matter of seconds the SIEM solution is able to recognize patterns in malicious events and triggers alerts when incidents are recognized. Previously, with a non-SIEM solution, this correlation could take hours.
SIEM streamlines the process by parsing relevant information and displaying it in an easily manageable format. The client’s front end can then be used to access relevant log events. From there you can quickly search for more events based on device criteria, such as source IP, destination IP, hostname, etc., and determine how the malicious traffic entered the network as well as the severity of the threat.
Key Takeaways
If your organization is still managing logs from a number of independent locations and struggling to correlate data between various devices, it is time to consider switching to a SIEM solution. Here are a few things to think about when planning your next move.
Weeding Out False Positives
The consolidation of log events allows SIEM to correlate data and discover false positive. The classification of false positives allows you to remove unwarranted incidents from your alerts. This ensures that you will not waste time constantly reacting to false positives or ‘noise’ within your environment.
Addressing Real Threats
For real threats, you can utilize SIEM to identify each device involved in an incident. From there you are able to strategize your responses to the threat. Doing this quickly and efficiently can mean the difference between a major outbreak on a network and a minor isolated, remediated incident.
Cost-savings
SIEM is a cost saver. Between the time saved managing alerts and incidents and the mitigation of a critical data breach, SIEM is a viable business decision.






